Showing posts with label windows basics. Show all posts
Showing posts with label windows basics. Show all posts
Friday 6 July 2012
Command to Hide/Unhide a File
Command to Hide: Attrib +h "PathofFile"
Command to Unhide: Attrib -h "PathofFile"
Tuesday 26 June 2012
Application Packaging Interview Questions - Windows Basics
Application Packaging Interview Questions related to Windows Basics
Windows Basics
- Explain Windows Installer(MSI) architecture
- Can we make Operating system not to install MSIs?
- How to set Windows to create log files automatically when MSIs are installed?
- What is the use of MSIs present in C:\Windows\Installer folder?
- How to identify if a setup is installing drivers?
- What is a host file? Can we include host file inside MSI?
- What are Environment Variables, and what is their usage?
- Name the locations where Environment Variables can be found on Windows OS?
- How to find whether a Setup is a Legacy or MSI?
- Disadvantages of Legacy apps?
- Advantages of MSI apps?
- Disadvantages of MSI apps?
- What is the use of Windows Installer Service?
- What is ActiveSetup?
- Is ActiveSetup part of MSI or Windows OS?
- What is Run Key?
- What is the difference Run, RunOnce and ActiveSetup?
- What is a File Association or File Extension?
- What is a ProgID?
- What is Windows Registry or simply Registry?
- How are HKCR and HKLM related?
- How are HKCU and HKU related?
- What is SID? and what is present inside SID?
- What is the location of ARP entries in Registy?
- Where are services located in registry?
- What is ODBC?
- What ODBC entries are required by an application to successfully connect to Database?
- Versions of WindowsXP, Vista, 7, 2003 Server, 2008 Server Operating Systems?
- Difference between WindowsXP and Windows7?
- Is it possible to install MSI file on clean Windows98 system? and why?
- When was MSI technology came into existence?
- What is Event Viewer?
- command to identify SID of currently logged in user?
- Can we install two MSIs at a time? and why?
- Registry Path for ProductCodes of MSIs installed on Windows?
- What is System Account on Windows?
- Which is master account on Windows?
- What is the extension of shortcut file ?
- How to remove small "arrow" mark for shortcuts on desktop?
- How to make an application not to create an entry in Add/Remove Programs?
- How to hide Remove Button for application entry in ARP using Registry?
- How to hide Change/Modify Button for application entry in ARP using Registry?
- How to hide Repair Button for application entry in ARP using Registry?
- Location of AllUsers desktop shortcuts on WindowsXP and Windows7?
- Location of AllUsers StartMenu shortcuts on WindowsXP and Windows7?
- What are Local, LocalLow, Roaming folders on Windows 7? and how they are related to WindowsXP folders?
- What is UAC in Windows7?
- What is session zero isolation in Windows7?
- How to set UAC not be displayed for installing MSIs?
- Differences between 32it and 64bit Operating Systems?
- How to identify if a application is 32bit or 64bit ?
- Where are 32bit files stored in 64bit OS?
- Where are 32bit application related registries stored on 64bit OS HKLM registry?
- How to detect if OS is 32bit or 64bit?
- Command to Shutdown computer on WinXP and Win7?
- Command to Restart computer on WinXP and Win7 ?
- What is DLL hell?
- What is Windows File Protection? What is the location where Windows protected files are stored?
- What is File Versioning?
- If a machine has DLL of version 2.0 and your application has same DLL with version 3.0, what happens to the file during installation ?
Search this blog for Answers
Friday 22 June 2012
How to hide Drives in My Computer?
Create registry as described below:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer
Name: NoDrives
Data Type: REG_DWORD
Value: varies - see below
To calculate the value to use, add up the following codes for the drives that you want to hide:
A=1
B=2
C=4
D=8
E=16
F=32
For instance to hide the E and F drives, the value would be 48
Wednesday 11 April 2012
Microsoft UE-V
Microsoft User Experience Virtualization (UE-V) is an enterprise-scale user state virtualization solution that provides users a consistent, personal Windows experience that matches their unique work style. UE-V is simple and versatile so IT professionals can enable the personal, user-defined experiences across many devices while maintaining oversight. It can also integrate into existing management tools and infrastructure, which make it easily scale to the needs of any size organization.
Please use following URL to download UE-V
https://connect.microsoft.com/MDOPTAP/UEV
Please use following URL to download UE-V
https://connect.microsoft.com/MDOPTAP/UEV
Tuesday 6 September 2011
Windows File Versioning Rules
At the core of any installer is the actual installation of files. But determining whether to install a file is a complex process. At the highest level, making the determination depends on whether the component to which a file belongs is marked for installation. Once the determination is made that a file should be copied, the process is complicated if another file with the same name exists in the target folder. In such situations, making the determination requires a set of rules involving the following properties:
Highest Version Wins — All other things being equal, the file with the highest version wins, even if the file on the machine has the highest version.
Versioned Files Win — All other things being equal, a versioned file gets installed over a non-versioned file.
Favor Product Language — All other things being equal, if the file being installed has a different language than the file on the machine, favor the file with the language that matches the product being installed. Language neutral files are treated as just another language so the product being installed is favored again.
Mismatched Multiple Languages — All other things being equal, after factoring out any common languages between the file being installed and the file on the machine, any remaining languages are favored according to what is needed by the product being installed.
Preserve Superset Languages — All other things being equal, preserve the file that supports multiple languages regardless of whether it is already on the machine or is being installed.
Non-versioned Files Are User Data — All other things being equal, if the Modified date is later than the Create date for the file on the machine, do not install the file because user customizations would be wiped out. If the Modified and Create dates are the same, install the file. If the Create date is later than the Modified date, the file is considered unmodified, install the file.
Non-versioned Files Using Companion — All other things being equal, a non-versioned file that is associated with a versioned file using the companion mechanism abides by the rules for the versioned file. The only exception is if the versioned file on the machine and the versioned file being installed have the same version and language but the companion file is missing on the machine. In this case the companion file being installed is used even though the versioned file on the machine is used.
Rules Are Global — The rules for determining when to install a file reside in one place within the installer and are global, meaning they apply to all files equally.
- Version
- Date
- Language
Highest Version Wins — All other things being equal, the file with the highest version wins, even if the file on the machine has the highest version.
Versioned Files Win — All other things being equal, a versioned file gets installed over a non-versioned file.
Favor Product Language — All other things being equal, if the file being installed has a different language than the file on the machine, favor the file with the language that matches the product being installed. Language neutral files are treated as just another language so the product being installed is favored again.
Mismatched Multiple Languages — All other things being equal, after factoring out any common languages between the file being installed and the file on the machine, any remaining languages are favored according to what is needed by the product being installed.
Preserve Superset Languages — All other things being equal, preserve the file that supports multiple languages regardless of whether it is already on the machine or is being installed.
Non-versioned Files Are User Data — All other things being equal, if the Modified date is later than the Create date for the file on the machine, do not install the file because user customizations would be wiped out. If the Modified and Create dates are the same, install the file. If the Create date is later than the Modified date, the file is considered unmodified, install the file.
Non-versioned Files Using Companion — All other things being equal, a non-versioned file that is associated with a versioned file using the companion mechanism abides by the rules for the versioned file. The only exception is if the versioned file on the machine and the versioned file being installed have the same version and language but the companion file is missing on the machine. In this case the companion file being installed is used even though the versioned file on the machine is used.
Rules Are Global — The rules for determining when to install a file reside in one place within the installer and are global, meaning they apply to all files equally.
Windows File Protection
A common problem in the history of the Microsoft Windows operating systems has been the ability for shared system files to be overwritten by non-operating system installation programs. After such changes are made, the user may experience unpredictable system performance, ranging from application errors to operating system crashes. This problem affects several types of files--most commonly dynamic link libraries (.dll) and executable files (.exe).
In Windows 2000 and Windows XP, the Windows File Protection (WFP) feature prevents overwriting or replacement of certain system files. Overwriting shared system files can result in unpredictable system performance that ranges from application errors to operating system crashes. System instability caused by non-standard replacement of system files has been a common problem. By preventing the replacement of these essential system files, file version mismatches are avoided, and the overall stability of the system is improved.
In Windows 2000 and Windows XP, the Windows File Protection (WFP) feature prevents overwriting or replacement of certain system files. Overwriting shared system files can result in unpredictable system performance that ranges from application errors to operating system crashes. System instability caused by non-standard replacement of system files has been a common problem. By preventing the replacement of these essential system files, file version mismatches are avoided, and the overall stability of the system is improved.
ActiveSetup Implementation
If you are using Windows Installer for per-machine-based installations, it could be the case that your setup contains components with user-related resources that have no entry-points to initiate the install-on-demand/self healing function of MSI. This, of course, will mean that when deployed the package will not install the user resources required to run the application properly.
But wait, don’t lose hope! In such a case you can use the Active Setup for a self healing on demand. It needs just one registry key in your msi file.
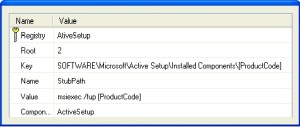
This registry key can be assigned to any Component that installs per-machine resources or you can create one component just for this key.
How it works:
The value in the StubPath key will be executed at a special time during which the Active Setup tasks are running and no other Windows Installer processes are running in the background that could cause the repair not to run (which would be the case if you attempted to run this command in the Run-Once registry key).
The command will thereby perform a repair for HKCU registry keys and missing files.
If this command runs successfully, it will create a registry key in HKCU and the command will not run again. However, if you wish to trigger this command again, because of a small update, then use the Version Key and increment its value each time you wish to run this command again when a user logs in.
Important Note:
Remember to use this command only if your setup does not contain any entry-point that would not allow the repair on demand, because this repair will run when a user on the target workstation logs in after the installation has been run. That means, even if the user doesn’t use the installed application, it will run the repair. And as you may already know, those repairs can take some time depending on the workstation’s hardware configuration and the size of the package.
SetACL Permissions Examples
Using SetACL to provide permissions
Command1: Providing registry permissions to Authenticated Users group
1. setacl.exe "MACHINE\SOFTWARE\AHouse\GEPUIS ORBIX" /registry /grant "Authenticated Users" /full /i:cont_obj_inh /p:yes /r:cont_obj /silent
OR using S-ID
"MACHINE\SOFTWARE\AHouse\GEPUIS ORBIX" /registry /set "S-1-5-11" /full /sid /silent
Command2: Providing Folder permissions to Authenticated Users group
setacl.exe "c:\AudioTools\GIMP" /dir /set "S-1-5-11" /change /sid /silent
Change the group name / S-ID according to your requirement
Why multiple MSIExec.exe processes running on machine during aninstallation
A number of MSIExec processes can be running during an installation. The reason for this is that Windows Installer uses a client-server model for performing installations. Additionally for security reasons, Windows Installer hosts DLL and script custom actions in a "sandbox" process. Depending on how the install was initiated, one of the MSIExec processes can be the client process. Another MSIExec process is Windows Installer service. Any remaining MSIExec processes are usually sandbox processes for hosting custom actions. The determination as to which MSIExec process will serve as the sandbox process for a script or DLL custom action depends in part on whether the custom action will run elevated or impersonated and whether the custom action is 32-bit or 64-bit.
Monday 5 September 2011
Windows Intune
Your employees depend on you to keep their PCs running at their best, whether they are in the office or on the road. Windows Intune simplifies and helps businesses manage and secure PCs using Windows cloud services andWindows 7. The Windows Intune cloud service delivers management and security capabilities through a single Web-based console so you can keep your computers and users operating at peak performance from anywhere. Give your users the best Windows experience with Windows 7 Enterprise or standardize your PCs on the Windows version of your choice. Windows Intune fits your business by giving you big tech results with a small tech investment. The result? Less hassle, and peace of mind knowing that your employees' PCs are well-managed and highly secure.
Windows Intune can be used by in-house IT professionals or by solution providers to manage the PCs of multiple businesses.
Whether you are in search of a solution that can deliver the essentials of management and protection for all your PCs or just those hard-to-reach PCs—highly distributed workers, non-domain joined PCs, field employees, or recent acquisitions—Windows Intune can help.
For more information please visit http://www.microsoft.com/windows/windowsintune/pc-management.aspx
Windows Intune can be used by in-house IT professionals or by solution providers to manage the PCs of multiple businesses.
Whether you are in search of a solution that can deliver the essentials of management and protection for all your PCs or just those hard-to-reach PCs—highly distributed workers, non-domain joined PCs, field employees, or recent acquisitions—Windows Intune can help.
For more information please visit http://www.microsoft.com/windows/windowsintune/pc-management.aspx
Tuesday 30 August 2011
VBScript to Check 32bit or 64bit Operating System
VBScript to check if Operating Systems is 32bit or 64bit
Dim WshShell
Set WshShell = CreateObject("WScript.Shell")
Bits = GetObject("winmgmts:root\cimv2:Win32_Processor='cpu0'").AddressWidth
msgbox Bits
Hide ARP entry of an MSI
VBScript to hide ARP entry of an MSI. In place of [ProductCode] give the product code of the msi for which you want to hide the ARP entry.
Dim WSHShell,strRegKey
Set WSHShell = WScript.CreateObject("WScript.Shell")
WSHShell.Regwrite "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\[ProductCode]\SystemComponent","1","REG_DWORD"
VBScript to find MAC Address of a machine
VBScript to find the MAC Address of Network Adaptors attached to a computer.
On Error Resume Next
Dim strComputer
Dim objWMIService
Dim colItems
strComputer = "."
Set objWMIService = GetObject("winmgmts:" _
& "{impersonationLevel=impersonate}!\\" & strComputer & "\root\cimv2")
Set colItems = objWMIService.ExecQuery _
("Select * from Win32_NetworkAdapterConfiguration")
For Each objItem in colItems
Wscript.Echo "MAC Address: " & objItem.MACAddress
Next
VBScript to Check Free Disk Space
Following script helps to find free disk space available on C-Drive, change the Drive letter in the script if you want to find free disk space of any other drive.
strComputer = "."
Set objWMIService = GetObject("winmgmts:\\" & strComputer & "\root\CIMV2")
Set colItems = objWMIService.ExecQuery( _
"SELECT * FROM Win32_LogicalDisk WHERE DeviceID = 'C:'",,48)
For Each objItem in colItems
Bytes = objItem.FreeSpace
If Bytes >= 1073741824 Then
SetBytes = Round(FormatNumber(Bytes / 1024 / 1024 / 1024, 2), 0) & " GB"
ElseIf Bytes >= 1048576 Then
SetBytes = Round(FormatNumber(Bytes / 1024 / 1024, 2), 0) & " MB"
ElseIf Bytes >= 1024 Then
SetBytes = Round(FormatNumber(Bytes / 1024, 2), 0) & " KB"
ElseIf Bytes < 1024 Then
SetBytes = Bytes & " Bytes"
Else
SetBytes = "0 Bytes"
End If
Wscript.Echo "OUTPUT = " & SetBytes
Next
How to Package Drive Applications using DPInst.exe
DPInst supports the following command-line switches that set the DPInst configuration flags that are described in Setting DPInst Configuration Flags and additional switches that further modify DPInst operation:
/a
The following command includes the /q command-line switch, which configure DPInst to operate in quiet-install mode. However, DPInst will operate in quiet-install mode only if aeula XML element is not included in a DPInst descriptor file. If a eula element is included, DPInst does not operate in quiet-install mode.
The following command includes a /se command-line switch, which suppresses the display of only the EULA page.
The following command includes the /q and /se command-line switches, which configure DPInst to operate in quiet-install mode, including suppressing the EULA page. The command also includes the /f command-line switch, which forces the installation of a new driver package for a device that is configured in a computer, even if the driver package that is currently installed on the device is a better match for the device than the new driver package.
The following command includes the /sh command-line switch, which configures DPInst to install a driver package on a device that is configured in a computer only if the new driver package is a better match for the device than the driver package that is currently installed on the device. This command facilitates using an installation package to batchinstall driver packages for devices that are configured in a computer. Although the installation package might contain a large number of driver packages, DPInst will install only driver packages that are better matches for the devices than the driver packages that are currently installed on the devices.
The following command includes the /u command-line switch, followed by the Abc.inf INF file, and the /d command-line switch. The /u command-line switch uninstalls the driver package that is associated with the Abc.inf INF file from all of the devices on which the package is installed. The /d command-line switch deletes the binaries that were copied to the system when the package was installed and deletes the package from the DIFx driver store. If the driver package is signed, the corresponding catalog file must be present in the same directory in which Abc.inf is located.
/a
- Sets the installAllOrNone flag to ON, which configures DPInst to install drivers in a driver package only if all of the drivers in the installation package can be installed.
- /c
- Configures DPInst, if DPInst is called at a command prompt, to display the text of log messages in the Command Prompt window.
- /d
- Sets the deleteBinaries flag to ON, which configures DPInst to delete the binary files that were copied to a system when a driver package was installed.
Note Starting with Windows 7, the /d switch is ignored by the operating system. Binary files, which were copied to a system when a driver package was installed, can no longer be deleted by using DPInst.
- /el
- Sets the enableNotListedLanguages flag to ON, which configures DPInst to enable all of the supported languages that are not explicitly enabled by language XML elements in a DPInst descriptor file.
- /f
- Sets the forceIfDriverIsNotBetter flag to ON, which configures DPInst to install a driver on a device even if the driver that is currently installed on the device is a better match than the new driver.
- /h, /?, or /help
- Configures DPInst to display help information about DPInst command-line options. If DPInst was called at a command prompt, DPInst displays the help text in the Command Prompt window; otherwise, DPInst displays the help text in a message box.
- /l language-ID
- Configures DPInst to display the text, bitmaps, and icon for the language that is specified by a language-ID value. The language-ID value can be specified in either hexadecimal or decimal format. For a list of the languages and corresponding language identifiers, see DPInst Localization Support.
If DPInst supports the specified language and runs on a Windows operating system in which the language is installed, DPInst will use the specified language. For more information about how to use the /L switch, see Testing Language Customization.
- /lm
- Sets the legacyMode flag to ON. In legacy mode, DPInst accepts unsigned driver packages without performing signature verification. However, be aware that Windows driver signing requirements apply to the installation of a driver package from the DIFx driver store. These requirements depend on the Windows version, the signature type, the driver package type, and the driver signing options that are set for a computer.
- /q or /s
- Sets the quietInstall flag to ON, which suppresses the display of wizard pages, user dialog boxes, and other user messages that DPInst and Windows generate. ThequietInstall flag works with the presence of an end-user license agreement (EULA) page and the suppressEulaPage flag.
- /p
- Sets the promptIfDriverIsNotBetter flag to ON, which configures DPInst to display a user dialog box if a new driver is not a better match to a device than a driver that is currently installed on the device. The user dialog box informs a user of this situation and provides an option to replace the driver that is currently installed on the device with the new driver.
- /path DPInst-working-directory
- Sets the DPInst working directory to DPInst-working-directory. DPInst searches for driver packages in the DPInst working directory and in subdirectories under the working directory that are specified by subDirectory XML elements in a DPInst descriptor file. For more information about how to set the DPInst working directory and specifying subdirectories under the working directory, see Specifying the Location of a Driver Package.
- /sa
- Sets the suppressAddRemovePrograms flag to ON, which configures DPInst to suppress the addition of entries to Programs and Features in Control Panel. These entries represent the driver packages and driver package groups that DPInst installs.
Note In versions of Windows earlier than Windows Vista, DPInst added the entry for the driver package or driver package group to Add or Remove Programs in Control Panel.
- /se
- Sets the suppressEulaPage flag to ON, which configures DPinst to suppress the display of a EULA page. The suppressEulaPage flag works with the quietInstall flag and the suppressWizard flag.
- /sh
- Sets the scanHardware flag to ON, which configures DPInst to install a driver package for a Plug and Play (PnP) function driver only if the driver package matches a device that is currently configured in a computer and if the driver package is a better match for the device than the driver package that is currently installed on the device.
- /sw
- Sets the suppressWizard flag to ON, which suppresses the display of wizard pages and other user messages that DPInst generates. The suppressWizard flag works with the presence of a EULA page and the suppressEulaPage flag.
- /u inf-file-path
- Configures DPInst to uninstall a driver package whose INF file is specified by inf-file-path. The path that is specified by inf-file-path is relative to the directory that containsDPInst.exe.
Examples
The following command includes the /q and /se command-line switches, which configure DPInst to operate in quiet-install mode, whether a eula XML element is included in a DPInst descriptor file. This command suppresses all of the wizard pages, user dialog boxes, and other user messages that DPInst and Windows generate.dpinst.exe /q /se
dpinst.exe /q
dpinst.exe /se
dpinst.exe /q /se /f
The following command includes the /u command-line switch, followed by the Abc.inf INF file, and the /d command-line switch. The /u command-line switch uninstalls the driver package that is associated with the Abc.inf INF file from all of the devices on which the package is installed. The /d command-line switch deletes the binaries that were copied to the system when the package was installed and deletes the package from the DIFx driver store. If the driver package is signed, the corresponding catalog file must be present in the same directory in which Abc.inf is located.
dpinst.exe /u abc.inf /d
Monday 29 August 2011
How To Register DLL
Following Command can be used to register DLL/OCX Files
regsvr32 /s <Path to DLL file to be registered>
Use, regsvr32 /? on command line to see more options available to register DLLs
regsvr32 /s <Path to DLL file to be registered>
Use, regsvr32 /? on command line to see more options available to register DLLs
MDOP 2011 R2
MDOP 2011 R2 is available and can be downloaded from theMicrosoft Volume Licensing website, MSDN and TechNet. This version of MDOP includes Microsoft BitLocker Administration and Monitoring (MBAM) which is brand new to MDOP, and updates to the Microsoft Diagnostic and Recovery Toolkit (DaRT) 7.0, and Microsoft Asset Inventory Service 2.0.
Difference between Run, Run Once, Active Setup
Active Setup:
It is used when your application requires installation of components such as files or registry keys on a per-user basis, but application has no advertised entry points or other triggers to initiate the installation process.
Run:
The Run key is processed after every logon, either by the Explorer shell, if it is present, or by First Boot Agent (FBA), if a custom shell, Command shell, or Task Manager Shell is used. If FBA processes this key, it does so after every logon, not during first boot as it normally would. Typically, this flag is used to load Systray applications, launch services in executables, hide autostart applications, or hide background processes
Run Once:
The RunOnce key is processed only once, by FBA, after Plug and Play device enumeration and DLL registration processing have completed. The values of this registry key are deleted from the registry after it is processed, so that it will not run again. Typically, this flag is used when a reboot is required, such as for a DLL or OCX registration, or for cleaning up a setup or an uninstall.
It is used when your application requires installation of components such as files or registry keys on a per-user basis, but application has no advertised entry points or other triggers to initiate the installation process.
Run:
The Run key is processed after every logon, either by the Explorer shell, if it is present, or by First Boot Agent (FBA), if a custom shell, Command shell, or Task Manager Shell is used. If FBA processes this key, it does so after every logon, not during first boot as it normally would. Typically, this flag is used to load Systray applications, launch services in executables, hide autostart applications, or hide background processes
Run Once:
The RunOnce key is processed only once, by FBA, after Plug and Play device enumeration and DLL registration processing have completed. The values of this registry key are deleted from the registry after it is processed, so that it will not run again. Typically, this flag is used when a reboot is required, such as for a DLL or OCX registration, or for cleaning up a setup or an uninstall.
Subscribe to:
Posts (Atom)